A real-world look at modern employee behavior, collapsed boundaries, and why being “not very strict”
about internet access is now a business liability in 2026.
Synopsis
This is not a thought experiment.
This is not a fringe opinion.
This is not “one bad employee.”
This is a real snapshot of how modern employees think about access, privacy, and corporate networks in 2026 —
and why that mindset is quietly becoming one of the most dangerous risks facing businesses.
This article is pro-business.
It is not an HR exercise.
It is a warning.
If this makes you uncomfortable, good.
That discomfort is still cheaper than a breach.
The Reddit Post Is Not the Problem — It’s the Symptom
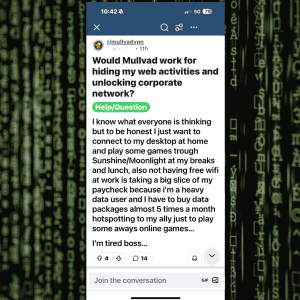
A real employee, in a public forum, asks whether using a privacy-focused VPN would allow them to:
- hide their internet activity from their employer
- bypass corporate web restrictions
- gain unrestricted and anonymous access
- remote into their home desktop
- avoid paying for their own mobile data
They are explicit about intent.
They are casual about it.
And they are not apologetic.
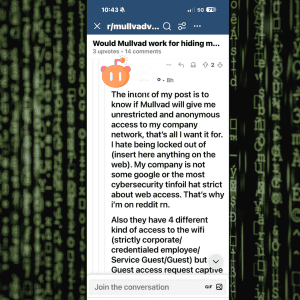
Then comes the most important line in the entire post:
“My company isn’t very strict about web access.”
That sentence is not a footnote.
It is the diagnosis.
Let’s Be Clear: This Is Not a Hacker Problem
There is no hoodie.
No dark web bravado.
No malicious language.
This is not an employee plotting an attack.
This is an employee openly stating:
“I want the business to get out of my way.”
That mindset is far more dangerous than overt hostility,
because it feels reasonable to the person holding it —
and invisible to leadership until something breaks.
WHY Employees Think This Way in 2026
1. Work From Home Is Over — But Many Never Accepted It
During the pandemic, businesses collapsed boundaries out of necessity.
Employees:
- worked from home
- used personal devices for business tasks
- mixed personal and corporate networks
- consumed personal content during work hours
Leadership called it flexibility.
Then offices reopened.
But psychologically, many employees never returned to
“this is not my network.”
To them:
- the office feels like an inconvenience, not a boundary
- corporate Wi-Fi feels like a utility, not a controlled asset
- restrictions feel arbitrary, not intentional
So when access is blocked, the reaction isn’t:
“Ah, policy.”
It’s:
“Why are they suddenly being difficult?”
2. TikTokification: Instant Gratification Meets Corporate Infrastructure
Modern employees are conditioned by digital platforms to expect:
- instant access
- zero friction
- immediate gratification
- endless workarounds
Every app teaches the same lesson:
If it doesn’t work instantly, bypass it.
That mindset doesn’t switch off at the office door.
VPNs, tunnels, hotspots, remote desktops, and browser tricks
are not seen as risky behavior.
They are seen as life hacks.
And life hacks are celebrated, not questioned.
3. “Not Strict” Means “Not Serious”
When an employee says:
“My company isn’t very strict about web access,”
they are not confessing.
They are explaining why they feel justified.
Loose enforcement, vague policies, selective discipline,
and fear of being “too strict” all send the same message:
Boundaries are optional.
Ambiguity is always interpreted as permission.
Controls that are not enforced are not controls at all.
Why This Is Bad for Business (In Real Terms)
Device Contamination
Employees bypass controls to:
- install pirated IPTV apps
- download cracked software
- run free game launchers
- access sketchy streaming sites
These are malware delivery systems, not entertainment.
Once that device reconnects to your corporate network,
the contamination comes with it.
Credential Theft & Session Hijacking
Free VPNs and shady tunnels exist for one reason:
data collection.
They:
- log credentials
- inject malicious traffic
- downgrade encryption
- harvest sessions
An employee routing corporate traffic through these tools
is not protecting privacy.
They are outsourcing trust to whoever is on the other end.
Legal and Financial Exposure
Piracy on corporate infrastructure is not an employee issue.
It is a business liability.
- ISP complaints
- DMCA notices
- regulatory scrutiny
- insurance complications
You don’t get to claim ignorance.
It’s your network.
Silent Compromise
The most damaging breaches don’t look dramatic.
They look like:
- normal logins
- normal hours
- normal traffic
- legitimate users
By the time something looks wrong,
the damage is already done.
The Absurdity Gap That Explains Everything
Recent workplace surveys and culture research show
Gen Z expectations around workplace comfort, autonomy,
and personal accommodation that would have been unthinkable
in prior generations.
Including discussions suggesting employers should provide
private spaces on business property to accommodate employees’
personal needs during the workday.
Laugh if you want.
But understand what it signals.
The same mindset that says:
“The workplace should fully adapt to my personal life”
is the mindset that says:
- network restrictions are unreasonable
- monitoring is intrusive
- policy is negotiable
- convenience outweighs control
This didn’t appear overnight.
It’s the result of boundaries that were never reset.
The Truth Businesses Need to Hear
If your security strategy depends on employees:
- agreeing with restrictions
- understanding threat models
- respecting invisible boundaries
Then it isn’t a strategy.
It’s hope.
And attackers don’t care how reasonable your people are.
They care how easy you are to blend into.
The Business Takeaway
You cannot outsource discipline to employees.
You cannot educate your way out of entitlement.
You cannot culture your way around predictable behavior.
You must:
- establish hard boundaries
- enforce them consistently
- remove ambiguity
- design security for misuse, not compliance
Anything else is negligence dressed up as flexibility.
Final Word
That Reddit post is not shocking.
It is inevitable.
This is how employees think in 2026.
This is how attackers exploit it.
And this is why businesses keep getting blindsided.
The companies that survive won’t be nicer.
They’ll be clearer.
Comment Policy
This discussion is intended for business owners, executives, and public-sector leaders.
Comments that add insight, challenge assumptions, or advance the conversation are welcome.
Promotional posts, links, generic praise, marketing pitches, or off-topic commentary will be removed.
Comments that demonstrate clear thought and experience will be approved.
Moderation is intentional.
Quality beats volume.
